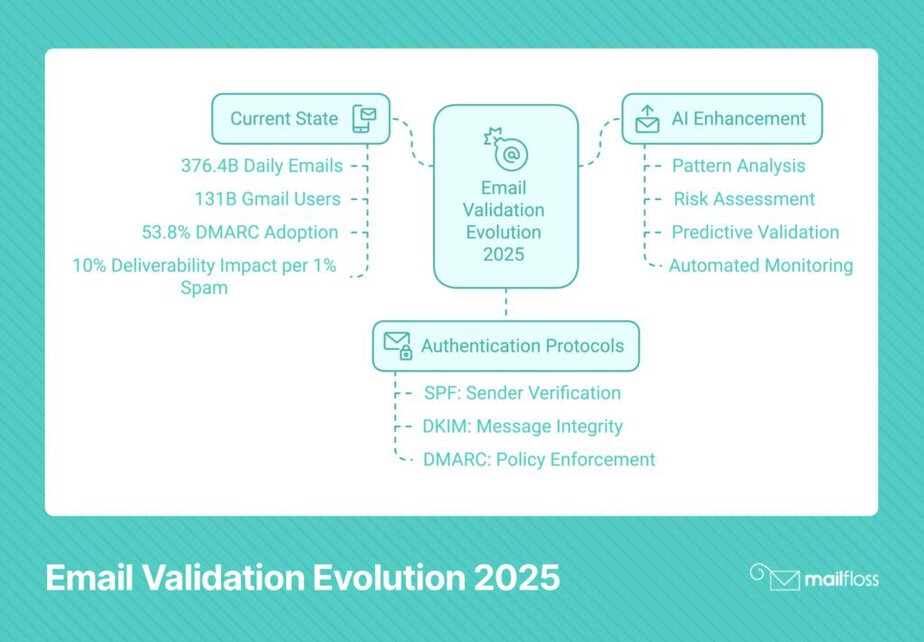
Email validation might seem straightforward, but getting it right can make or break your email marketing success. By 2026, an estimated 376.4 billion emails will be sent daily, with approximately 131 billion using Gmail alone (Source: Clean Email).
This massive volume makes proper email validation more crucial than ever for maintaining strong email deliverability.
We've seen firsthand how invalid emails can wreak havoc on marketing campaigns. A single percentage point increase in spammy addresses can torpedo your deliverability by 10%. That's why we're sharing our battle-tested validation strategies that keep email lists clean and campaigns performing at their peak.
This guide cuts through the complexity of email validation, focusing on practical test cases that work in real-world scenarios. We'll explore everything from basic syntax checks to advanced AI-powered verification methods, helping you build a robust validation system that protects your sender reputation and maximizes email deliverability.
Whether you're dealing with existing lists or implementing new signup forms, you'll discover exactly how to validate emails effectively while avoiding common pitfalls that could damage your email marketing success.
Ready to master email validation?
Revolutionizing Email Validation with AI and Machine Learning
AI-powered email validation transforms how we verify email addresses in 2025. By 2026, email validation services will increasingly leverage AI algorithms to improve validation accuracy and automate decision-making processes (Source: Allegrow). This shift from basic syntax checking to intelligent verification represents a significant leap forward in email verification technology.
Smart validation systems now analyze multiple data points simultaneously. These systems examine email syntax, domain reputation, mailbox existence, and historical engagement patterns. This comprehensive approach significantly reduces the risk of accepting invalid or potentially harmful email addresses.

Implementing Smart Validation Systems
Modern email verification goes beyond simple regex patterns. Real-time validation APIs now integrate seamlessly with signup forms and CRM systems, providing instant feedback on email validity. These systems detect subtle patterns that might indicate disposable email services or high-risk addresses.
Risk analysis has become a central component of advanced validation. Machine learning algorithms evaluate historical data patterns to identify potentially problematic email addresses before they impact your sender reputation. This proactive approach prevents delivery issues rather than merely reacting to them.

Automation plays a crucial role in modern validation systems. These tools continuously monitor email list health, automatically flagging and removing problematic addresses. This ongoing maintenance ensures your email lists remain clean without requiring constant manual intervention.
The integration capabilities of modern validation tools extend beyond basic verification. They connect with popular email service providers, CRM systems, and marketing platforms, creating a seamless validation ecosystem. This interconnected approach ensures consistent verification across all customer touchpoints.
Mastering Email Authentication in 2025
Email authentication protocols form the backbone of reliable email validation. In 2024, 53.8% of senders reported using DMARC for email authentication, representing an 11% increase from 2023 (Source: Mailgun). This growing adoption highlights the critical role of proper authentication in maintaining strong sender reputation.
Authentication Protocol Synergy
SPF, DKIM, and DMARC work together to create a robust email authentication framework. Each protocol serves a specific purpose while complementing the others. Understanding this synergy helps implement a comprehensive validation strategy that maximizes email deliverability.
SPF verification confirms whether sending servers are authorized to send emails for your domain. This protocol prevents email spoofing by creating a clear record of permitted sending sources. Configure your SPF record to include all legitimate email services while maintaining a strict sending policy.
DKIM adds a digital signature to your emails, ensuring they haven't been tampered with during transmission. Use at least a 2048-bit key for DKIM signatures to maintain strong security. Regular key rotation prevents potential security compromises while maintaining authentication integrity.
DMARC policies tie everything together by telling receiving servers how to handle authentication failures. Start with a monitoring policy before gradually increasing enforcement levels. This approach allows you to identify and fix issues before they affect email delivery.

Regular monitoring of authentication results provides valuable insights into email program health. Review DMARC reports to identify unauthorized sending attempts and authentication failures. This data helps maintain optimal authentication configuration while preventing potential delivery issues.
Authentication policies require regular maintenance to remain effective. Update records when adding or removing email services, and verify alignment between SPF, DKIM, and DMARC policies. This ongoing maintenance ensures consistent authentication performance across all email communications.

Building a Robust Validation Framework
Strategic email validation directly impacts deliverability success. A mere 1% increase in the number of spammy emails on your list can cause a 10% drop in deliverability (Source: LLC Buddy). This striking statistic emphasizes why proper email hygiene must be a cornerstone of your email marketing strategy.
Maintaining Validation Effectiveness
Regular validation maintenance prevents list quality degradation over time. Schedule automated validation checks at consistent intervals, focusing on both new subscriptions and existing contacts. This proactive approach identifies potential issues before they impact your sending reputation.
Implement validation checkpoints throughout your email collection process. Real-time validation at signup forms provides the first line of defense against invalid addresses. Secondary validation during list imports and regular maintenance checks create multiple layers of protection for your email program.
- Validate new addresses at point of collection
- Verify imported lists before first send
- Run quarterly validation on existing lists
- Monitor engagement patterns for early warning signs
Quality assurance extends beyond basic validation checks. Monitor bounce rates, engagement metrics, and spam trap hits to maintain optimal list health. These indicators help identify potential validation gaps or emerging issues requiring attention.
Automation streamlines the validation process while improving accuracy. Configure your validation tools to automatically quarantine suspicious addresses and remove confirmed invalid ones. This systematic approach maintains list quality without requiring constant manual intervention.
Data-driven validation strategies improve over time through performance tracking. Monitor key metrics like validation accuracy, false positive rates, and detection of problematic patterns. Use these insights to refine your validation rules and improve overall effectiveness.
Integration between validation systems and email platforms ensures consistent quality control. When validation tools communicate directly with your email service provider, they can automatically update list segments and trigger necessary cleanup actions. This seamless connection maintains list hygiene while reducing manual workload.
Common Validation Mistakes and Solutions
Validation errors can severely impact email marketing success. Repeatedly sending emails to invalid or harmful addresses can cause ESPs to flag your domain, lowering your ability to reach recipients (Source: Allegrow). Understanding and avoiding these common pitfalls helps maintain strong email deliverability.
Prevention and Recovery Strategies
Authentication misalignments often stem from incomplete protocol implementation. Ensure all authentication records align properly, including SPF, DKIM, and DMARC policies. This alignment prevents delivery issues while maintaining strong sender authentication.
Configuration errors frequently occur during validation setup. Common mistakes include overly strict regex patterns that reject valid addresses and loose patterns that allow invalid ones. Balance validation rules to catch problematic addresses without blocking legitimate subscribers.
Security oversights can expose your email program to risks. Regular monitoring helps identify potential blacklist issues or spam trap hits early. This vigilance allows for quick corrective action before serious delivery problems develop.
- Monitor authentication alignment regularly
- Test validation rules against known good addresses
- Implement gradual policy changes
- Maintain detailed validation logs
Early warning systems help identify potential issues before they escalate. Track validation failure patterns, bounce rates, and engagement metrics to spot emerging problems. This proactive approach prevents small issues from becoming major deliverability challenges.
Recovery procedures should focus on systematic problem resolution. When issues arise, investigate root causes rather than just treating symptoms. This thorough approach prevents similar problems from recurring while strengthening your overall validation system.
Future prevention relies on continuous system improvement. Regular audits of validation rules, authentication configurations, and monitoring systems help identify potential weaknesses. Address these areas proactively to maintain robust email validation effectiveness.
Preparing for Future Validation Challenges

Email validation continues to evolve with technological advancement. The rise of AI-powered verification systems, increasing email volumes, and emerging security threats require forward-thinking validation strategies. Understanding these trends helps prepare your email validation systems for future challenges.
Emerging Technologies and Adaptation
Machine learning algorithms increasingly power advanced validation systems. These tools analyze complex patterns in real-time, providing more accurate validation results while reducing false positives. Embracing these technologies positions your email program for continued success.
Integration capabilities become more crucial as email ecosystems grow more complex. Modern validation systems must communicate seamlessly with various platforms and services. This interconnected approach ensures consistent validation across all customer touchpoints.
Compliance requirements continue to evolve globally. Stay informed about emerging regulations affecting email validation and data protection. Regular updates to your validation processes ensure ongoing compliance while maintaining effective email verification.
- Implement scalable validation architecture
- Adopt AI-powered verification tools
- Monitor regulatory changes
- Maintain flexible integration options
Predictive analytics enhance validation accuracy by identifying potential issues before they occur. These tools analyze historical patterns and emerging trends to optimize validation rules automatically. This forward-looking approach helps maintain strong email marketing performance.
Security considerations become increasingly important as threats evolve. Implement robust encryption, regular security audits, and comprehensive monitoring systems. These measures protect your validation infrastructure while ensuring data privacy compliance.
Automation capabilities continue expanding, reducing manual intervention requirements. Modern validation systems handle routine tasks automatically, allowing teams to focus on strategic improvements. This efficiency enables better resource allocation while maintaining validation effectiveness.
Frequently Asked Questions About Email Validation
Understanding email validation complexities helps optimize your verification processes. Here are answers to the most common questions about email validation test cases and best practices.
How often should I validate my email list?
Validate new addresses in real-time during collection and perform full list validation quarterly. Monitor engagement metrics continuously and conduct additional validation when bounce rates increase or engagement decreases significantly.
What's the difference between syntax and mailbox validation?
Syntax validation checks email address format correctness, while mailbox validation verifies the actual existence of the email account. Both are essential components of a comprehensive validation strategy.
How do I implement DMARC without disrupting email delivery?
Start with a monitoring policy (p=none) to gather data about your email authentication. Gradually increase enforcement levels through quarantine to reject, allowing time to identify and fix any authentication issues.
Can AI-powered validation replace traditional methods?
AI-powered validation complements rather than replaces traditional methods. Combine both approaches for optimal results, using AI to enhance accuracy while maintaining fundamental validation checks.
Taking Your Email Validation to the Next Level
Effective email validation combines technical expertise with strategic implementation. From basic syntax checking to advanced AI-powered verification, each component plays a crucial role in maintaining list quality and ensuring delivery success.
We understand the challenges of managing email validation in today's complex digital landscape. That's why we've developed automated solutions that handle validation complexities while you focus on growing your business. Ready to strengthen your email validation? Check out our comprehensive validation solutions designed for modern email marketing needs.
Start implementing these best practices today to improve your email deliverability, protect your sender reputation, and maximize your email marketing success. Remember, effective email validation isn't just about preventing problems—it's about building a foundation for sustainable email marketing growth.